Mario: You can’t defend. You can’t prevent. The only thing you can do is detect and respond. By Bruce Schneier
Introduction
Cyber criminals, driven by financial gain, political motives, or pure malice, use increasingly sophisticated techniques to compromise the security of networks and systems. Among the most common attack vectors are vulnerabilities in the supply chain, zero-day exploits, and malicious insiders or targeted phishing campaigns. This article will explore these attack methods and finally offer strategies to protect against these complex threats.
1. Vulnerabilities in the Supply Chain: A Hidden Entry Point
What is a supply chain attack? Cybercriminals often target the weakest links in the supply chain, exploiting third-party vendors and software dependencies to infiltrate otherwise secure networks.
Software dependencies and third-party risks Attackers may inject malicious code or exploit vulnerable libraries, impacting a wide range of products that depend on these components.
Notable supply chain attacks (e.g., Log4J, XZ) Real-world examples demonstrate how attackers can compromise entire ecosystems by targeting just one dependency.
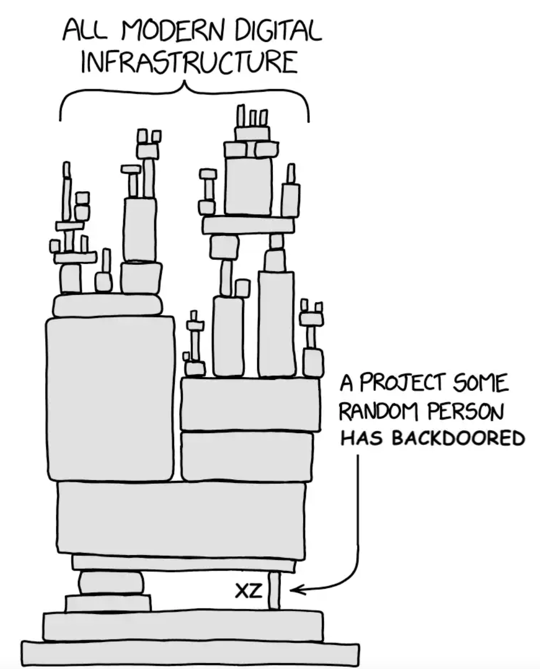
The xz backdoor has brought up an even more disturbing ramification of this situation, which is that a malicious entity (e.g. a nation-state) can create a persona (or multiple), build trust with the random guy maintaining the library since 2003, eventually take over the project, then implant a backdoor that targets core software like OpenSSH. The only reason we just avoided one of the largest cyber incidents in history is because one guy running Debian Sid noticed sshd using a bit more CPU than normal while he was benchmarking something completely unrelated.
2. Zero-Day Exploits: Leveraging Unknown Vulnerabilities
What are zero-day vulnerabilities? A zero-day exploit takes advantage of software vulnerabilities that are unknown to the vendor and, therefore, lack a patch.
The zero-day market: From criminal groups to nation-state actors Explore the underground economy of zero-day vulnerabilities, where exploits are traded and sold.
High-profile zero-day attacks (e.g., Stuxnet) Examples of how zero-day vulnerabilities have been used to disrupt critical infrastructure.
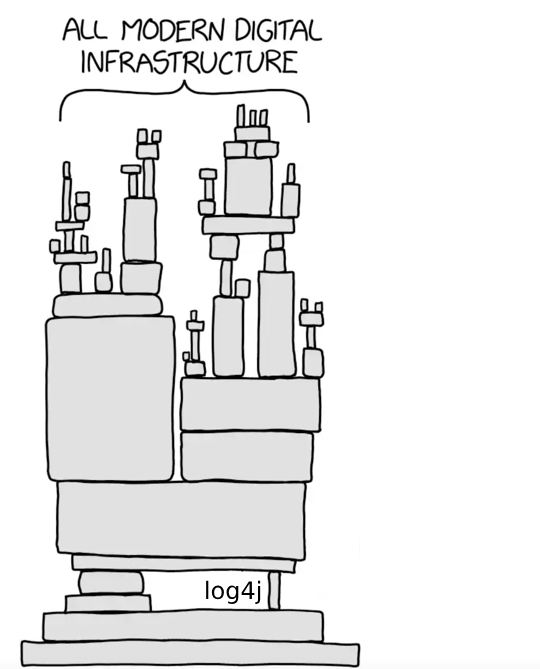
On December 9, 2021, security researchers discovered a flaw in the code of a software library used for logging. The software library, Log4j, is built on a popular coding language, Java, that has widespread use in other software and applications used worldwide. This flaw in Log4j is estimated to be present in over 100 million instances globally. If exploited, could permit a remote attacker to execute arbitrary code on vulnerable systems. This library had one maintainer who lived in the outback.
3. The Human Factor: Insider Threats and Phishing Campaigns
The weakest link: Human error and malicious insiders Employees, whether intentionally malicious or just careless, are often the easiest targets for attackers.
Phishing and spear phishing Analysis of common tactics used to deceive employees and gain access to sensitive information.
The problem of malicious insiders Insight into how disgruntled employees or insiders with access can pose severe threats to an organization.
4. Lateral Movement: Spreading Through the Network
- What is lateral movement? Once inside a network, attackers move laterally to gain access to more valuable assets and escalate their privileges.
Mario: You’re wondering to yourself: How can I protect my business? You can’t :) But you can detect and respond.
Simple solution to a complex problem just use Beelzebub 😀!
Beelzebub, won’t be used by anyone, it won’t generate log noise, and the first event on the honeypot will indicate that someone has infiltrated the infrastructure.