Blog
Articles about honeypots, malware analysis, and other cyber security topics.
Securing AI Agents with Honeypots
This article explores the Beelzebub MCP honeypot system that transforms AI agent security by deploying deceptive functions to detect and analyze sophisticated prompt injection attacks in real-time.
user: Mario Candela, date: 05/07/2025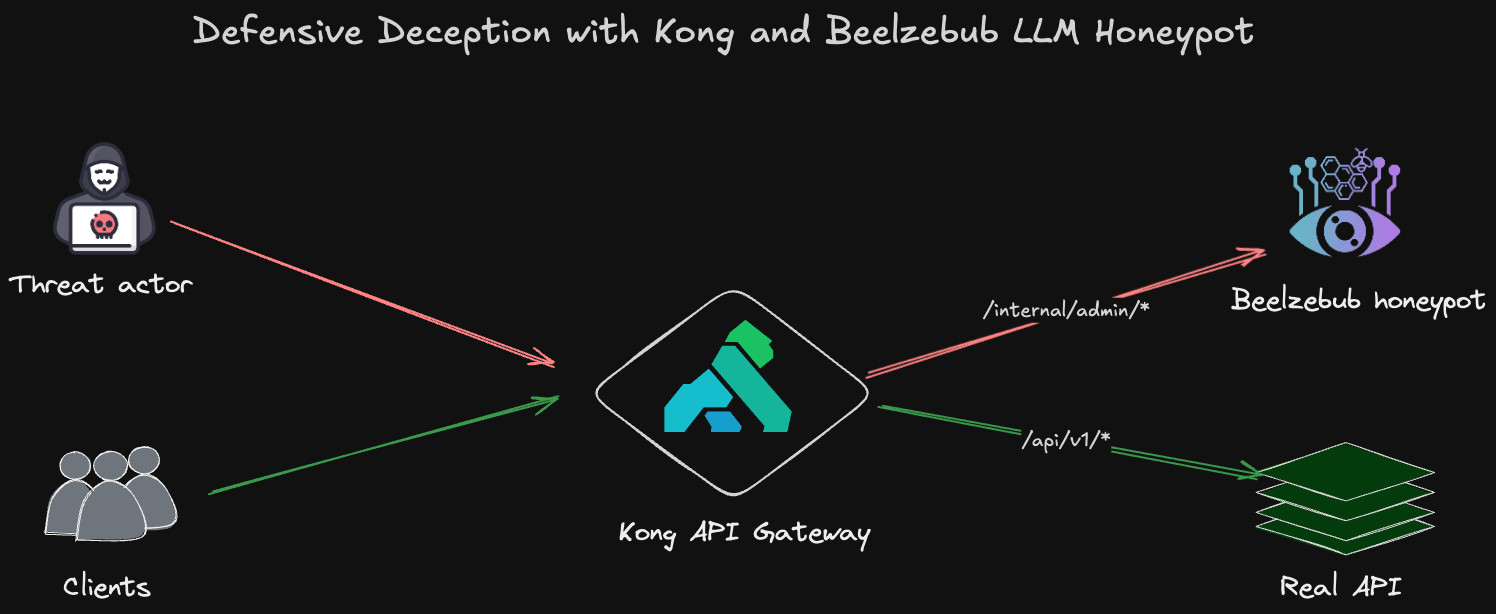
Defensive Deception with Kong and Beelzebub LLM Honeypot
This article explores the innovative approach that transforms your existing Kong infrastructure into a powerful threat intelligence platform for modern cloud-native environments.
user: Mario Candela, date: 06/04/2025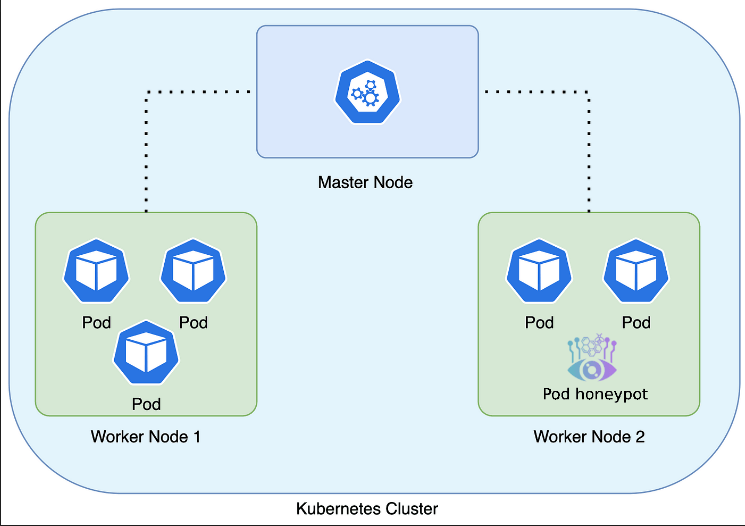
Securing Kubernetes: Using Honeypots to Detect and Prevent Lateral Movement Attacks
This article examines lateral movement threats in Kubernetes clusters and demonstrates how to configure and deploy the Beelzebub honeypot system using Helm to detect and prevent these attacks.
user: Mario Candela, date: 30/03/2025
How cybercriminals make money with cryptojacking
Catch a crypto jacking malware and analyze how cybercriminals make money with it using a LLM honeypot.
user: Mario Candela, date: 08/02/2025
SSH LLM Honeypot caught a real threat actor
Discover how a real threat actor was captured and analyzed using an SSH LLM honeypot.
user: Mario Candela, date: 24/12/2024
LLM Honeypot
LLM Honeypot with Beelzebub framework
user: Mario Candela, date: 25/06/2024
How cybercriminals attacks your company
How cybercriminals attacks your company
user: Mario Candela, date: 08/10/2024